This article explains how to hide confidential information for an ASP.NET Core app on a development machine. We will learn about Secret Manager in .NET Core.
As we know, the ASP.Net Core application comes with appsettings.json file. This file contains basic configurable information about the project. Some developers store database connection strings with passwords and some third-party API credentials. The best practice says, never store passwords or other delicate information in any file within the source code.
In an ASP.Net Core application, we will need to ensure certain bits of application information, such as user secrets, that we are not supposed to share with any other people. Your secret information may include database connection details, third-party API credentials, and API keys.
At the point when we share the project with others or push the source code to a source control like TFS or GitHub then we are also sharing this secret data with other people.
How can we avoid this?
A feature in ASP.NET Core named Secret Manager allows you to store user secrets outside your source code.
What is a Secret Manager?
We store confidential information on the applications using Secret Manager in a .NET Core project. It keeps the app secret in a different location and not in the project location. The app secrets are related to a particular application or shared across several .Net Core projects. The app secrets aren’t a part of source control so they are not checked into source control.
The Secret Manager tool doesn’t encode the stored data. It’s for application development purposes only. It keeps keys and values in a JSON-based file in the user profile directory.
How does a secret manager work?
The Secret Manager tool hides the details, for example, where and how the confidential data are put away. You can utilize the tool without knowing these execution details. The data are put away in a JSON document in the local machine’s user profile folder:
In Windows Machine, the secrets.json file path is –
%APPDATA%\Microsoft\UserSecrets\<user_secrets_id>\secrets.jsonHere, <user_secrets_id> is a unique Guid.
How to create User Secrets in .NET Core with Visual Studio?
I have created a .Net Core application in Visual Studio. To add User Secrets in the .Net Core application, follow the below steps.
- Open Visual Studio 2019 or 2022.
- Create a project. We can choose the .NET Web API Project.
- Right-click on the project name in Solution Explorer.
- Select Manage User Secrets.
- Now cut the connection string node from the
appsettings.jsonfile and paste it into thesecrets.jsonfile. - Build the project and run the application. It should work perfectly.
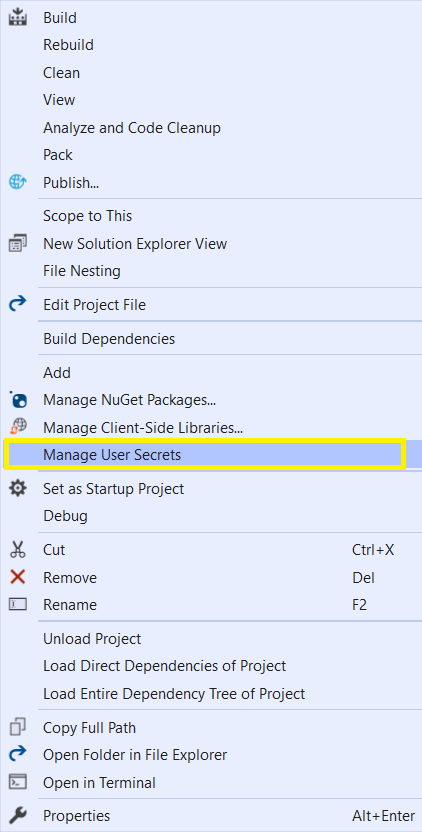
This is to note that, the secrets.json file is not part of the project. So, whenever we share the project or we add the project to source control, we are not sharing the database connection string or confidential information available in secrets.json with others.
Manage User Secret with Developer Powershell
Instead of writing anything into the secrets.json file, we can use the Developer PowerShell command in Visual Studio to write our confidential information to the secrets.json file:
dotnet user-secrets init
dotnet user-secrets set "key" "value"To view the list of user secrets, use the below command:
dotnet user-secrets listNote: This feature is only available for your local development machine and not for UAT or Production.
Summary –
Secret Manager is a feature in .Net Core which helps us to hide confidential information from others. It works only on development machines. In this way, we will not share confidential information such as database connection or API client secret even if we share the project and the source code.
Hope you like this article. Please write down your feedback in the comment box below.


Leave a Reply